
Cyber Security: What does it means for Business?
August 01, 2022 · Mr. Suraj
Business data is more vulnerable than ever before. Cyber security is necessary to efficiently operate business—but it’s also critical for protecting customers’ information.
Cybersecurity is important because it protects all categories of data from theft and damage. This includes sensitive data, personally identifiable information (PII), protected health information (PHI), personal information, intellectual property, data, and governmental and industry information systems. Without a cybersecurity program, an organization cannot defend itself against data breach campaigns, which makes it an irresistible target for cybercriminals.
Both inherent risk and residual risk are increasing, driven by global connectivity and usage of cloud services, like AWS, Azure, to store sensitive data and personal information. Widespread poor configuration of cloud services paired with increasingly sophisticated cyber criminals means the risk that your organization suffers from a successful cyber-attack or data breach is on the rise.
Business leaders can no longer solely rely on out-of-the-box cybersecurity solutions like antivirus software and firewalls, cybercriminals are getting smarter and their tactics are becoming more resilient to conventional cyber defenses. It's important to cover all the fields of cybersecurity to stay well-protected.
When creating cyber security procedures, it’s helpful to use a layered security model. This model begins with the internet and ends with employees.
Employee Education
Most major security breaches involve an employee action that enabled hackers to gain access to the system. Employees must be educated on Cyber security best practices. As per report by Tessian (IT Security Firm) combined survey data and insights from Stanford University professor Jeff Hancock, 88% of data breaches are caused by human error outright.
Nearly half of the employees in Tessian’s survey say “they are “very” or “pretty” certain they have made a mistake at work that had security repercussions for themselves or their company”. One in four employees said they have clicked on a phishing email at work. Men were twice as likely as women to fall for phishing scams, with 34% of male respondents saying they have clicked on a link in a phishing email, versus just 17% of women. Older employees were the least susceptible to phishing scams, with just 8% of workers over 51 saying they had clicked on a phishing link.

Researchers suggest companies might need to tailor security training to different age groups if they want the teachings to stick. Furthermore, not all employees are cybersecurity savvy. Also give training on impact of Social Engineering to business, weak passwords, Do’s and Don’ts while handling business data.
As per ‘Cost of Data Breach report – 2021’ based on IBM Security analysis of the research data compiled by the Ponemon Institute IBM Security, some of the findings are as below:
10% Increase in avg. total cost of a breach 2020-2021
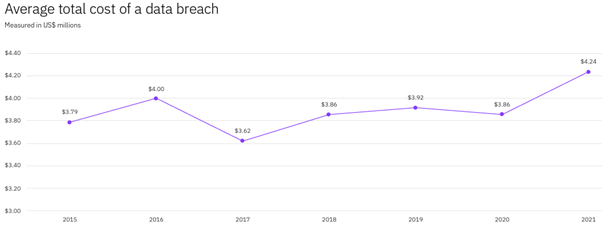
The average total cost of a data breach increased by the largest margin in seven years. Data breach costs increased significantly year-over year from the 2020 report to the 2021 report, increasing from $3.86 million in 2020 to $4.24 million in 2021.
- 11 Consecutive years healthcare had the highest industry cost of a breach.
- 38% Lost business share of total breach costs.
- $180 Per record cost of personally identifiable information
- 20% share of breaches caused compromised credentials
- 287 Avg. number of days to identify and contain a data breach.
- 80% Cost difference where security AI and automation was fully deployed vs. not deployed.
- $4.62m Avg. total cost of a ransomware breach.
Endpoint Security
An endpoint protection platform is a vital part of enterprise cybersecurity for several reasons. First of all, in today’s business world, data is the most valuable asset of a company and to lose that data, or access to that data, could put the entire business at risk of insolvency. Businesses have also had to contend with not only a growing number of endpoints, but also a rise in the number of types of endpoints. These factors make enterprise endpoint security more difficult on their own, but they’re compounded by remote work and BYOD policies—which make perimeter security increasingly insufficient and create vulnerabilities. The threat landscape is becoming more complicated, as well: Hackers are always coming up with new ways to gain access, steal information or manipulate employees into giving out sensitive information. Add in the opportunity, cost of reallocating resources from business goals to addressing threats, the reputational cost of a large-scale breach, and the actual financial cost of compliance violations, and it’s easy to see why endpoint protection platforms have become regarded as must-haves in terms of securing modern enterprises.
Data breaches can be far more than a temporary terror — they may change the course of your life. Businesses, governments, and individuals alike can experience huge complications from having sensitive information exposed. Whether you are offline or online, hackers can get to you through the internet, Bluetooth, text messages, or the online services that you use.
Without proper attention to detail, a small vulnerability can cause a massive data breach.
Since many people are unaware of how common modern security threats work, they don’t give it enough attention.
Endpoint security components
Typically, endpoint security software will include these key components:
- Machine-learning classification to detect zero-day threats in near real time.
- Advanced antimalware and antivirus protection to protect, detect, and correct malware across multiple endpoint devices and operating systems.
- Proactive web security to ensure safe browsing on the web.
- Data classification and data loss prevention to prevent data loss and exfiltration.
- Integrated firewall to block hostile network attacks.
- Email gateway to block phishing and social engineering attempts targeting employees.
- Actionable threat forensics to allow administrators to quickly isolate infections.
- Insider threat protection to safeguard against unintentional and malicious actions.
- Centralized endpoint management platform to improve visibility and simplify operations.
- Endpoint, email and disk encryption to prevent data exfiltration
Network Security
Network security is one of the most important aspects to consider when working over the internet, LAN or other method, no matter how small or big your business is. While there is no network that is immune to attacks, a stable and efficient network security system is essential to protecting business data. A good network security system helps business reduce the risk of falling victim of data theft and sabotage.
Network security is enforced using a combination of hardware and software network tools. The primary goal of network security is to prevent unauthorized access into or between parts of a network. Network segmentation is often used to achieve this. Network segmentation is the division of networks and the designation of resources to those divisions.
A security official, or group of them, determines security strategies and policies that keep the network safe and help the organization comply with security standards and regulations. It is the responsibility of everyone on the network to abide by these security policies. Every point in the network where an authorized user could access data is also a point where data could be compromised, either by a malicious actor or simply through a lack of diligence from the user. It also the responsibility of security tool vendors to update tools and software to stay ahead of evolving cyberthreats.
Network Security Components
Firewall:
Firewalls are some of the most widely used security tools and can be used at multiple different layers of the network. Are available in hardware/software model.
Intrusion prevention system (IPS):
This is a system designed to prevent intrusions. It actively removes unauthorized attempts to access a network.
Virtual Private Network (VPN)
This is a program that uses tunnelling protocols to encrypt information and send it over a public, less secure network.
Invest in Security
Business prosperity is directly proportional to the company’s profitability. The more security breaches it has, both offline and online, the less profitable the business stands to be since it will be losing money dealing with restoring systems and appeasing customers. Security is a preventative measure to ensure that the company can withstand attempts to get access to its data or premises. It is an investment that sees a return by allowing the business to be profitable instead of having to reinvest profits into mitigation and settlements. It might not be such a prominent contributor to the growth of an enterprise, but without security, the business would likely fail because of an inability to deal with the constant threats on its location or customer information.
Reference Links:
https://www.ibm.com/in-en/security/data-breach
https://www.tessian.com/resources/psychology-of-human-error-2022/
Quick Enquiry
To know more about Associated Chemicals feel free to send a message
 Our Sister Concerns
Our Sister Concerns 


Usefull Links
Get In Touch
Assochem Chambers, Bypass, Edapally,
Kochi-682024, Kerala, India.
Phones : +91 9495999349, +91 9388610189, +91 484 2339190, +91 484 2348028
E-mail : nsn@assochem.in, marketing@assochem.in, mail@assochem.in
Support

















